
This article explains, from a professional perspective:
-
El basic working principle of hotel key cards
-
El components of a hotel key card lock system
-
El full unlocking process
-
El security and encryption mechanisms involved
-
How the system integrates with Síndrome premenstrual software
-
The Basic Working Principle
When a guest taps or swipes their card, the hotel door lock reads encrypted information from the key card and compares it with the stored authorization data. If the data matches, the lock’s control module triggers the motor or solenoid to retract the latch — unlocking the door.
Technically, this is a process known as secure credential verification, consisting of the following steps:
-
El key card (or digital key) contains a unique ID and encrypted access data.
-
El door reader scans and retrieves that data.
-
El lock controller compares it with pre-stored authorization or PMS data.
-
Once verified, the system sends a signal to unlock the mechanism.
-
The event (user ID, time, result) is recorded in the log.
This entire process happens within 0.2–1.5 seconds, and the system can automatically recognize different roles — guests, housekeeping, or admin staff — ensuring both efficiency and security.
-
Components of a Hotel Key Card Lock System

A complete electronic hotel door lock system typically consists of the following core components:
-
Key Card (Credential)
Different technologies are used to store and transmit guest access data:
-
Magnetic Stripe Card – Encodes basic data like room number and validity; low security and easily demagnetized.
-
RFID Card (MIFARE series) – Contains an embedded chip and unique ID; popular models include MIFARE Clásico y MIFARE DESFire EV2/EV3, supporting AES encryption for higher security.
-
Llave móvil (NFC/BLE) – Guests receive a digital key through a mobile app and can unlock their room using their smartphone.
The reader detects and interprets the data from the card or phone:
-
Activates when the card is near.
-
Reads and verifies card ID or encrypted data;
-
Sends the data to the controller for validation.
-
Door Lock Controller
This is the “brain” of the lock:
-
Stores encrypted keys and authorization lists;
-
Executes the verification and unlocking decision;
-
Logs all access records (time, user type, result).
-
Management Software (Síndrome premenstrual / Access System)
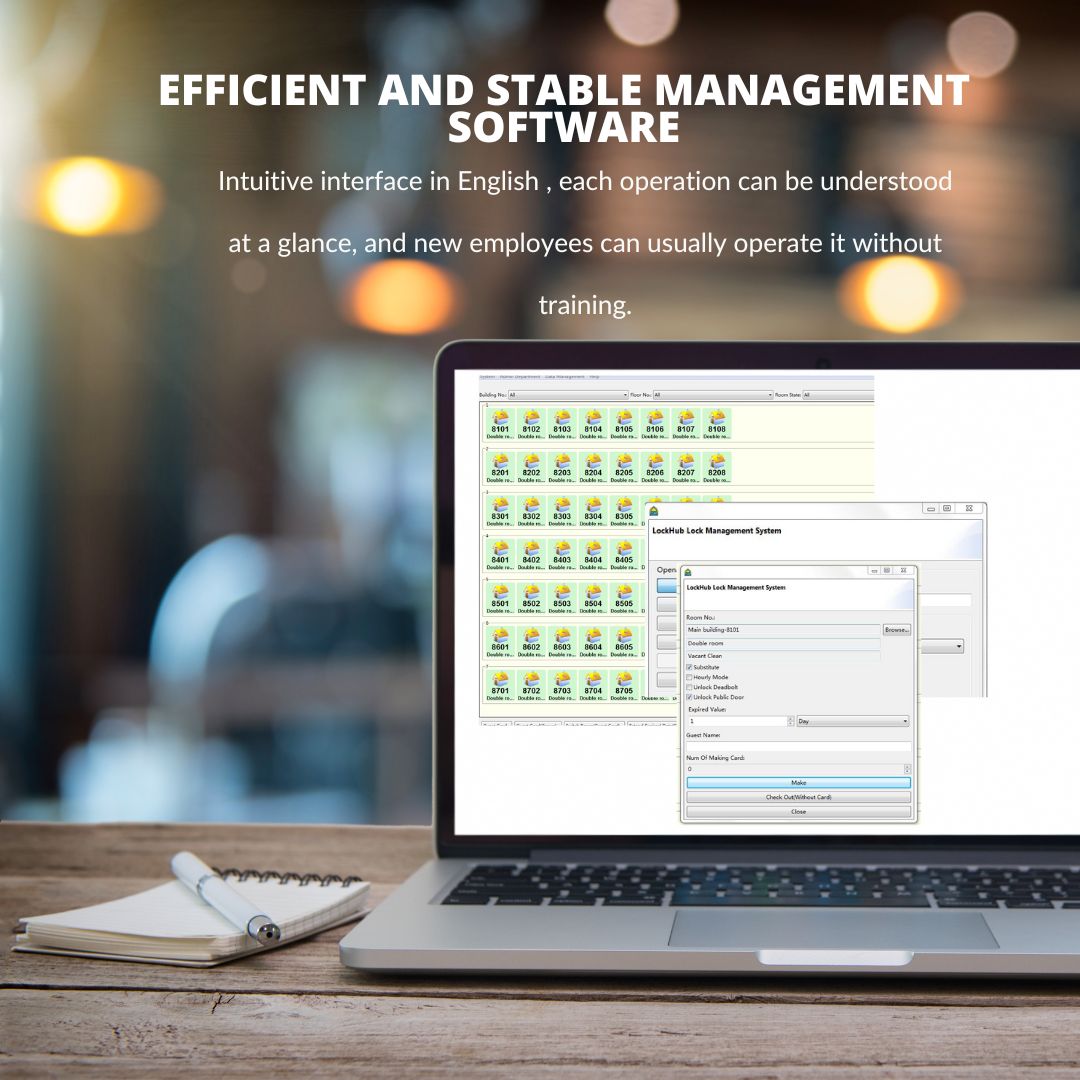
Software de cerradura de puerta de hotel YonAnn
The hotel’s Sistema de gestión de propiedades (Síndrome premenstrual) communicates with the lock software to:
-
Encode new cards or mobile keys;
-
Manage guest check-in/check-out data;
-
Automatically deactivate expired or lost keys;
-
Generate access logs and reports.
-
Puerta and Cloud Server
These handle remote authorization, record uploads, and firmware updates.
They connect the on-site locks with the PMS or cloud system for centralized control.
-
Power & Mechanical Components
Most locks are powered by four AA batteries or rechargeable lithium packs. Emergency unlocking options — such as a mechanical key o external power port — are provided in case of battery failure.
-
Audit System
Each lock records its access events, including successful entries, failed attempts, and system errors. These records can be viewed locally or uploaded to the PMS for security auditing y incident tracking.
-
The Step-by-Step Unlocking Process
Let’s take an Cerradura de hotel RFID as an example to see what happens when you tap your key card:
Step 1: Activation
When the card approaches the reader, the RFID field energizes the chip in the card.
Step 2: Data Exchange & Anti-Collision
The reader establishes communication with the card and identifies its unique UID, ensuring there is no interference from other cards.
Step 3: Encrypted Verification
The system uses secure algorithms (e.g., AES) to decrypt and verify the card’s credentials, ensuring it’s not cloned or tampered with.
Step 4: Authorization Check
The controller checks if the card’s data, validity period, and access zone match the stored permissions (e.g., guest room, floor, gym).
Step 5: Unlock Execution
If authorized, the controller sends a signal to drive the motor to retract the latch. A green LED flashes, and the door unlocks. If invalid, the red LED flashes, and the event is logged.
Step 6: Record & Synchronization
The lock stores the access record locally and, when connected to the network, uploads the event data to the management system for review.
-
Security and Encryption Mechanisms
Modern hotel key card systems rely on multiple layers of encryption and protection to prevent unauthorized access or duplication.
-
Identity Verification & Mutual Authentication
High-end hotel locks adopt two-way authentication:
-
The card must prove its authenticity to the lock.
-
The lock must also prove its legitimacy to the card, preventing “man-in-the-middle” attacks.
-
Encryption Algorithms
-
MIFARE DESFire EV2/EV3 uses AES encryption for secure communication.
-
Mobile keys employ dynamic tokens or one-time passwords to prevent replay attacks.
-
Hierarchical Gestión de claves
System master keys are stored securely within encrypted hardware modules, while each room has a unique sub-key — isolating potential security breaches.
-
Anti-Cloning & Anti-Relay Mechanisms
-
Nonce-based (random) authentication ensures each transaction is unique.
-
Expiration and usage limits prevent prolonged unauthorized access.
-
Locks feature tamper alarms and log every attempt.
-
Security Auditing
Every event — successful or failed — is recorded.
The PMS can analyze abnormal access attempts or repeated failures, alerting management automatically.
-
Integration with the Property Management System (Síndrome premenstrual)
-
Síndrome premenstrual Integración Workflow
-
Guest makes a reservation — PMS creates a booking.
-
The front desk or kiosk encodes the key card or sends a mobile key.
-
Access data (room number, check-in/check-out time) is written to the credential.
-
PMS synchronizes authorization with the network or gateway.
-
The guest uses the card or phone to unlock the door during their stay.
-
Card Deactivation & Security
When the guest checks out, the PMS automatically invalidates the card.
If a card is lost, it can be remotely deactivated immediately through the PMS to prevent misuse.
-
Online vs. Offline Operation
-
Online Locks: Connected to the cloud for instant authorization updates.
-
Offline Locks: Operate independently, syncing data periodically.
-
Hybrid Systems: Combine both — offering reliability and centralized management. Most modern hotels choose hybrid solutions for better flexibility and stability.
-
Communication Protocols
Common protocols include:
-
RS485 / Wiegand – communication between lock and control unit;
-
TCP/IP / MQTT – secure data transmission between lock and server;
-
API / SDK – for third-party software integration and customized applications.
-
The Future: Smart, Secure, and Connected
Hotel key card systems are evolving rapidly, moving toward smart and cloud-connected ecosystems. Emerging trends include:
-
Smartphone-based NFC/BLE keys;
-
Cloud-based key management and remote authorization;
-
OTA firmware updates and real-time alerts;
-
AI-powered access analytics and energy management.
Como profesional fabricante de cerraduras inteligentes, Cerradura inteligente YonAnn provides comprehensive solutions — from hardware to software — including:
-
RFID hotel locks, Bluetooth smart locks, and digital room number systems;
-
PMS and API integration;
-
OEM/ODM customization for hotel and apartment projects worldwide.
Conclusión

Understanding how a hotel key card system works — from the access principle to encryption and PMS integration — helps hoteliers enhance both security and guest experience.
Choosing a professional lock supplier is key to achieving this balance. At Cerradura inteligente YonAnn, we make hotel access management smarter, safer, and more efficient — combining technology with comfort for every stay.

